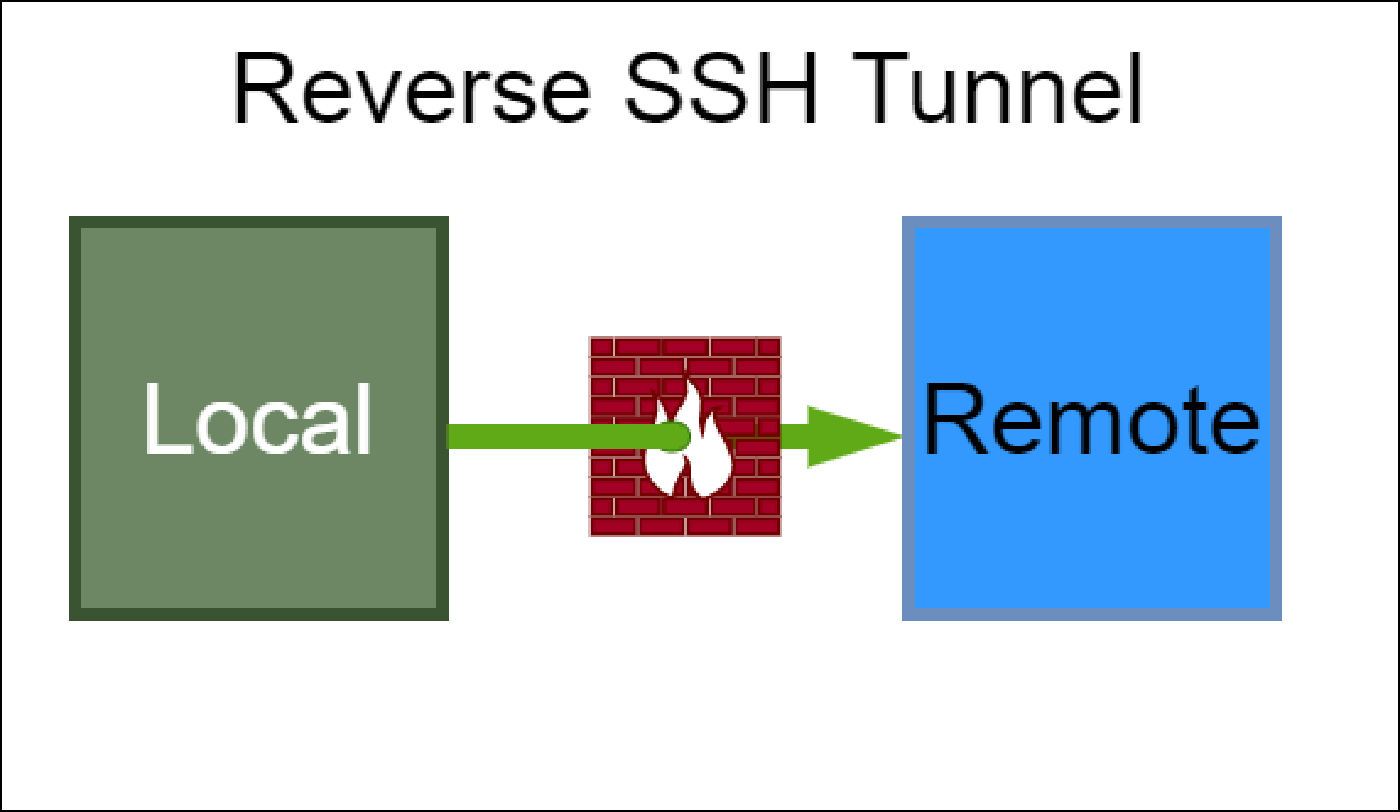
SSH Reverse Tunnel
SSH Tunnel
A reverse SSH tunnel allows a local service to be securely accessible by a remote connection.
Understanding Reverse SSH Tunnels
Service on local computer that is running on port 80. Want to access this service from a remote computer, but a firewall is in the way.
Setup
| Host Type | IP Address | Description |
|---|---|---|
| Internal | 192.168.1.6 | Internal IP address of the local service |
| Public | 159.223.180.93 | public IP address of the remote server |
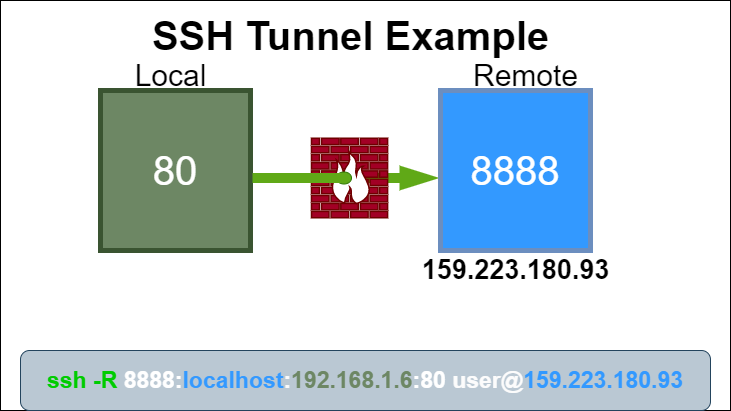
Reverse SSH Tunnel Example
Confirm listening ports
Local:
Local server running web server on port 80 and ssh on port 22.
> netstat -ntl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 :::80 :::* LISTEN
Remote:
Remote client running SSH services
> netstat -ntl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
Establishing a reverse SSH tunnel:
From the local server run the following command to establish a SSH tunnel:
ssh -N -R localhost:8888:192.168.1.6:80 root@159.223.180.93
-Nis a flag to just forward ports and not execute remote commands-Ris the reverse SSH tunnel flag that forwards remote connections to the local side- localhost is the host on the remote server that will bind to the local service
8888is the port that the remote server will listen on- 192.168.1.6 is the internal IP address of the local service
- 80 is the port of the local service
- root is the SSH user of the remote server
- 159.223.180.93 is the public IP address of the remote server
Confirm listening ports
Local
Local host no change on listening services.
> netstat -ntl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 :::80 :::* LISTEN
Remote
After executing the reverse SSH tunnel command, the local service at 192.168.1.6:80 will be accessible on the remote machine at localhost:8888.
> netstat -ntl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8888 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 ::1:8888 :::* LISTEN
Shorthand
Remote command execution or pseudo terminal will be allocated for this connection.
ssh -R 8888:localhost:80 root@159.223.180.93
Change the port number for other services.
- Don’t need to include localhost of the local machine because it is default
- Default SSH port is 22, so don’t need to specify this
-Nflag is optional. Functionality will be the same
Summary
Greate way to access service on local computer that is running on port 80 that is running behind a firewall to access this service from remote computer.
Check out:
Related Posts
2023 Phoenix VMUG UserCon
Introduction: The recent 2023 Phoenix VMUG UserCon brought together some like-minded people in the field, with discussions ranging from VMware technologies to best practices for optimizing existing systems.
Read moreRed Hat User Group Insights, Ansible Automation Platform, and ITSM Integration
Introduction: This blog post aims to summarize the key takeaways from this informative workshop. At the recent Red Hat User Group workshop on Red Hat Insights, Red Hat Ansible Automation Platform, and their integration with management (ITSM) systems, such as ServiceNow, provided valuable insights into how these technologies work together.
Read moreRobocopy Examples
Robocopy Examples Robocopy has many command line options and it can be overwhelming to know which commands to use. In this post, we will take a look at how to ues robocopy to copy, mirror, purge Files and Folders.
Read more